The AWS Certified Security – Specialty certification is a highly respected credential for cloud professionals aiming to demonstrate their expertise in securing complex AWS environments. It’s designed for individuals with a deep understanding of security principles, including data protection, identity and access management, incident response, and compliance. With cloud security becoming a top priority across industries, earning this certification can significantly elevate your professional credibility and career prospects. In this blog, we’ll walk you through the essential steps, strategies, and resources you need to prepare effectively and confidently pass the AWS Security Specialty exam.
Cloud security is no longer just a feature—it’s a frontline business priority. As organizations continue to move their critical workloads to the cloud, the demand for security professionals who understand how to secure AWS environments has skyrocketed. If you’re aiming to stand out in the cybersecurity landscape, the AWS Certified Security–Specialty certification offers one of the most prestigious validations of your cloud security expertise.
But make no mistake, this is not an entry-level certification. The exam tests your ability to think like a security architect: to protect data, ensure compliance, detect threats, and respond with precision. It demands a deep understanding of AWS services, layered security strategies, encryption techniques, identity and access controls, and incident response workflows.
Earning this credential is not just about passing an exam, it’s about proving that you can design and implement security solutions in a dynamic and scalable cloud environment. And with AWS being the most widely adopted cloud provider globally, this certification can open doors to high-impact, well-compensated roles across industries. In this guide, we will break down everything you need to prepare for and pass the AWS Certified Security – Specialty exam in 2025: from the exam structure and core domains to preparation tips, study resources, and real-world insights that help you succeed with confidence.
AWS Security Specialty Exam Overview
The AWS Certified Security – Specialty exam is a certification exam for IT professionals who want to demonstrate their expertise in securing AWS workloads. The exam covers a range of security-related topics, including:
- Identity and Access Management (IAM)
- Detective Controls
- Infrastructure Security
- Data Protection
- Incident Response
- Compliance
To pass the AWS Certified Security – Specialty exam, candidates must demonstrate a deep understanding of these topics and how to apply them to secure AWS workloads. The exam consists of 65 multiple-choice and multiple-response questions, and candidates have 130 minutes to complete the exam.
The AWS Certified Security – Specialty exam is designed for experienced IT professionals who have hands-on experience with AWS security services, and a strong understanding of security best practices. To prepare for the exam, candidates should study the official AWS documentation, enroll in an AWS certification course, use practice exams, and focus their studies on the exam objectives.
EXAM DETAILS
| Exam Code | SCS-C01 |
| Exam Type | Speciality |
| Exam Duration | 170 minutes |
| Exam Codt | $300 USD |
| Exam Format | Multiple Choice questions and Multiple Responses |
| Exam Scoring | Scaled score from 100 to 1000 |
| Passing Score | 75% – 80% |
| Exam Language | English, Japanese, Korean and Simplified Chinese |
Exam Question Format
AWS Certified Security Specialty questions comes with two questions types,
- There will be multiple choice questions in which you only have select one correct option out of four options.
- And multiple responsive questions in which there can be multiple correct answers from the options given.
Exam Score Guidelines
- In AWS Security Specialty exam certification you can select one or more best suitable answers depends on the type of questions.
- In AWS exam no marks will be deducted on giving wrong answer.
- There may be some content in the exam which does not have any score, it is just for gathering general information and it will not have any effect on the exam.
Exam Result Process
- Score is scaled between 100 to 1000.
- On percentage basis you need to score between 75% to 80%.
- AWS Security Specialty exam is based on pass or fail format. And also the exam result will be mailed to you within five business days from the day of the exam.
- For this exam you just have to get the overall passing score so it is not necessary to pass each section.
- Each section in this exam has a varying weighting, with differ in number of questions listed against each section in the exam.
Examination Retake policy
Amazon has rules for retaking the certification test. According to the policy, you must wait 14 days before retaking the test. There is no such limit on how many times you can take the exam; you can keep taking it until you pass and are certified. Moreover, you are required to pay the entire registration price for each try.
How to register?
- You need to register first and then sign in to aws.training.
- After that, click on Certification on the top of the page.
- Then click on AWS Certification account, Schedule new exam.
- Check for the exam you want to take and click schedule at Pearson VUI button or PSI.
And at the time of exam before entering the test center you are required to provide two government issued ID’s with matching your name on it as on the application form.
AWS Security Specialty Skills Required
- You should have at least two years of hands on experience in securing AWS workloads.
- It is also recommended to have 5 years of experience in IT security for designing and implementing security solutions.
- This exam will examine your knowledge about how to secure AWS platform.
- You should have a good understanding in data encryption methods, secured internet protocols and AWS mechanism for implementing them.
- It also recommended having working knowledge of security services of AWS, specialized data classification and mechanism of AWS data protection.
- You should have experience of 2 or more years in production deployment for using AWS security services.
- A good knowledge of operations and risk in security.
AWS Certified Security Specialty Exam Glossary
Get familiarity with the services and important terms –
Identity and Access Management (IAM)
- IAM – A service used to manage users, groups, roles, and their permissions.
- IAM Policy – A JSON document that defines permissions for users or services.
- IAM Role – A way to grant temporary access to AWS resources for users or services.
Encryption and Data Protection
- KMS (Key Management Service) – AWS-managed service to create and manage cryptographic keys.
- CMK (Customer Master Key) – The main encryption key used with KMS.
- Envelope Encryption – Encrypting data using a data key, which itself is encrypted with a master key.
- SSE (Server-Side Encryption) – AWS encrypts data at rest within services like S3, RDS, etc.
Monitoring and Logging
- AWS CloudTrail – Captures all API calls and activity across your AWS account.
- Amazon CloudWatch – Provides monitoring and alerting for AWS resources.
- VPC Flow Logs – Captures network traffic flow data in your VPC.
- AWS Config – Evaluates and monitors the configuration of AWS resources over time.
Infrastructure Security
- Security Groups – Virtual firewalls that control inbound/outbound traffic to AWS resources.
- NACLs (Network Access Control Lists) – Stateless firewalls for subnets within a VPC.
- AWS WAF (Web Application Firewall) – Protects web applications from common attacks.
- AWS Shield – Provides protection against Distributed Denial of Service (DDoS) attacks.
- Amazon Inspector – Scans EC2 instances for vulnerabilities.
Compliance and Risk Management
- AWS Artifact – Central location for compliance-related reports and documents.
- Shared Responsibility Model – Clarifies which security responsibilities AWS manages and which the customer must handle.
- Data Classification – Identifying data sensitivity levels to apply proper protection.
Incident Response
- Runbooks/Playbooks – Documented procedures for responding to incidents.
- Amazon GuardDuty – Threat detection and continuous security monitoring service.
- Amazon Macie – Uses machine learning to identify and protect sensitive data, like PII, in S3.
- AWS Security Hub – Aggregates findings from security services into a unified dashboard.
Networking and Connectivity
- VPC (Virtual Private Cloud) – A logically isolated section of AWS used to launch resources.
- VPN and Direct Connect – Secure, private connections between your data center and AWS.
- PrivateLink – Enables private connectivity between VPCs and AWS services without using public IPs.
Other Key Concepts
- S3 Bucket Policies – JSON-based policies that control access to Amazon S3 buckets.
- ACL (Access Control List) – A legacy method for managing S3 permissions.
- Trusted Advisor – Provides real-time insights and recommendations on security, cost, and performance.
Why choose the AWS Security Specialty Exam?

The AWS Certified Security – Specialty certification is important for IT professionals who want to demonstrate their expertise in securing AWS workloads. This certification is highly valued by organizations that use AWS as it demonstrates a deep understanding of the security features and capabilities of the AWS platform. Some benefits of earning the AWS Certified Security – Specialty certification include:
- Career advancement: The AWS Certified Security – Specialty certification is recognized as a benchmark of expertise in securing AWS workloads, and can help IT professionals advance their careers and increase their earning potential.
- Increased credibility: The AWS Certified Security – Specialty certification provides IT professionals with an industry-recognized credential that demonstrates their expertise in securing AWS workloads. This credibility can help IT professionals stand out in a competitive job market.
- Improved job performance: The AWS Certified Security – Specialty certification provides IT professionals with a deep understanding of security best practices and AWS security services. This knowledge can help IT professionals improve their job performance and deliver more secure AWS workloads.
- Access to new job opportunities: The AWS Certified Security – Specialty certification opens up new job opportunities for IT professionals in the growing field of cloud security.
- Staying current with AWS updates: Earning the AWS Certified Security – Specialty certification requires staying current with updates to the AWS platform, which can help IT professionals stay current with the latest security features and capabilities of AWS.
Overall, the AWS Certified Security – Specialty certification provides IT professionals with the skills, knowledge, and credibility they need to succeed in the rapidly growing field of cloud security.
AWS Security Specialty (SCS-C01) Exam Layout
There are 6 domains to focus on in this Specialty Certification exam. Moreover, the Course Outline acts as the AWS certified security specialty exam blueprint.
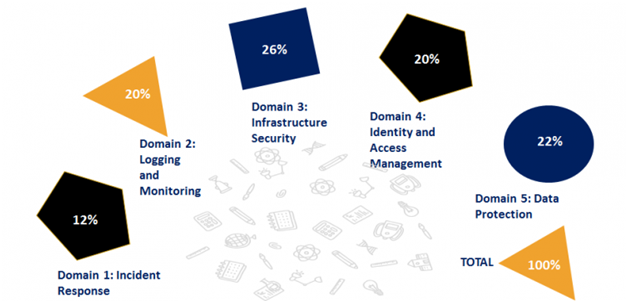
The AWS certified security specialty course covers the following domains:
Domain 1: Threat Detection and Incident Response (14%)
Task Statement 1.1: Design and implement an incident response plan.
Knowledge of:
- AWS best practices for incident response (AWS Documentation: AWS Security Incident Response Guide)
- Cloud incidents
- Roles and responsibilities in the incident response plan (AWS Documentation: Define roles and responsibilities)
- AWS Security Finding Format (ASFF) (AWS Documentation: AWS Security Finding Format (ASFF))
Skills in:
- Implementing credential invalidation and rotation strategies in response to compromises (for example, by using AWS Identity and Access Management [IAM] and AWS Secrets Manager) (AWS Documentation: Automatically rotate IAM user access keys at scale with AWS Organizations and AWS Secrets Manager)
- Isolating AWS resources (AWS Documentation: Design isolated resource environments)
- Designing and implementing playbooks and runbooks for responses to security incidents (AWS Documentation: Develop and test security incident response playbooks)
- Deploying security services (for example, AWS Security Hub, Amazon Macie, Amazon GuardDuty, Amazon Inspector, AWS Config, Amazon Detective, AWS Identity and Access Management Access Analyzer) (AWS Documentation: Security, identity, and compliance)
- Configuring integrations with native AWS services and third-party services (for example, by using Amazon EventBridge and the ASFF)
Task Statement 1.2: Detect security threats and anomalies by using AWS services.
Knowledge of:
- AWS managed security services that detect threats (AWS Documentation: Monitoring data security with managed AWS security services)
- Anomaly and correlation techniques to join data across services (AWS Documentation: Concepts for anomaly or outlier detection)
- Visualizations to identify anomalies
- Strategies to centralize security findings (AWS Documentation: Centralized Security Management)
Skills in:
- Evaluating findings from security services (for example, GuardDuty, Security Hub, Macie, AWS Config, IAM Access Analyzer) (AWS Documentation: AWS service integrations with AWS Security Hub)
- Searching and correlating security threats across AWS services (for example, by using Detective)
- Performing queries to validate security events (for example, by using Amazon Athena) (AWS Documentation: Querying AWS CloudTrail logs)
- Creating metric filters and dashboards to detect anomalous activity (for example, by using Amazon CloudWatch) (AWS Documentation: Using CloudWatch anomaly detection)
Task Statement 1.3: Respond to compromised resources and workloads.
Knowledge of:
- AWS Security Incident Response Guide (AWS Documentation: AWS Security Incident Response Guide)
- Resource isolation mechanisms (AWS Documentation: Design isolated resource environments)
- Techniques for root cause analysis (AWS Documentation: What is Root Cause Analysis (RCA)?)
- Data capture mechanisms (AWS Documentation: Capture data)
- Log analysis for event validation (AWS Documentation: Analyzing log data with CloudWatch Logs Insights)
Skills in:
- Automating remediation by using AWS services (for example, AWS Lambda, AWS Step Functions, EventBridge, AWS Systems Manager runbooks, Security Hub, AWS Config) (AWS Documentation: AWS Systems Manager Automation)
- Responding to compromised resources (for example, by isolating Amazon EC2 instances) (AWS Documentation: Remediating a potentially compromised Amazon EC2 instance)
- Investigating and analyzing to conduct root cause analysis (for example, by using Detective) (AWS Documentation: What is Amazon Detective?)
- Capturing relevant forensics data from a compromised resource (for example, Amazon Elastic Block Store [Amazon EBS] volume snapshots, memory dump) (AWS Documentation: Amazon EBS snapshots)
- Querying logs in Amazon S3 for contextual information related to security events (for example, by using Athena) (AWS Documentation: Querying AWS CloudTrail logs)
- Protecting and preserving forensic artifacts (for example, by using S3 Object Lock, isolated forensic accounts, S3 Lifecycle, and S3 replication) (AWS Documentation: Using S3 Object Lock)
- Preparing services for incidents and recovering services after incidents (AWS Documentation: Recovery)
Domain 2: Security Logging and Monitoring (18%)
Task Statement 2.1: Design and implement monitoring and alerting to address security events.
Knowledge of:
- AWS services that monitor events and provide alarms (for example, CloudWatch, EventBridge) (AWS Documentation: Alarm events and EventBridge)
- AWS services that automate alerting (for example, Lambda, Amazon Simple Notification Service [Amazon SNS], Security Hub) (AWS Documentation: Automated response and remediation)
- Tools that monitor metrics and baselines (for example, GuardDuty, Systems Manager)
Skills in:
- Analyzing architectures to identify monitoring requirements and sources of data for security monitoring (AWS Documentation: Designing and implementing logging and monitoring with Amazon CloudWatch)
- Analyzing environments and workloads to determine monitoring requirements (AWS Documentation: Perform an analysis on the workload demand)
- Designing environment monitoring and workload monitoring based on business and security requirements
- Setting up automated tools and scripts to perform regular audits (for example, by creating custom insights in Security Hub) (AWS Documentation: Custom insights)
- Defining the metrics and thresholds that generate alerts (AWS Documentation: Using Amazon CloudWatch alarms)
Task Statement 2.2: Troubleshoot security monitoring and alerting.
Knowledge of:
- Configuration of monitoring services (for example, Security Hub) (AWS Documentation: What is AWS Security Hub?)
- Relevant data that indicates security events (AWS Documentation: Logging and events)
Skills in:
- Analyzing the service functionality, permissions, and configuration of resources after an event that did not provide visibility or alerting (AWS Documentation: Refining permissions in AWS using last accessed information)
- Analyzing and remediating the configuration of a custom application that is not reporting its statistics (AWS Documentation: What Is AWS Config?)
- Evaluating logging and monitoring services for alignment with security requirements (AWS Documentation: Monitoring and Logging)
Task Statement 2.3: Design and implement a logging solution.
Knowledge of:
- AWS services and features that provide logging capabilities (for example, VPC Flow Logs, DNS logs, AWS CloudTrail, Amazon CloudWatch Logs) (AWS Documentation: Logging IP traffic using VPC Flow Logs)
- Attributes of logging capabilities (for example, log levels, type, verbosity) (AWS Documentation: AWS Lambda function logging in Python)
- Log destinations and lifecycle management (for example, retention period) (AWS Documentation: Managing your storage lifecycle)
Skills in:
- Configuring logging for services and applications (AWS Documentation: Configure service and application logging)
- Identifying logging requirements and sources for log ingestion
- Implementing log storage and lifecycle management according to AWS best practices and organizational requirements (AWS Documentation: Managing your storage lifecycle)
Task Statement 2.4: Troubleshoot logging solutions.
Knowledge of:
- Capabilities and use cases of AWS services that provide data sources (for example, log level, type, verbosity, cadence, timeliness, immutability) (AWS Documentation: AWS services for logging and monitoring)
- AWS services and features that provide logging capabilities (for example, VPC Flow Logs, DNS logs, CloudTrail, CloudWatch Logs) (AWS Documentation: Logging IP traffic using VPC Flow Logs)
- Access permissions that are necessary for logging (AWS Documentation: CloudWatch Logs permissions reference)
Skills in:
- Identifying misconfiguration and determining remediation steps for absent access permissions that are necessary for logging (for example, by managing read/write permissions, S3 bucket permissions, public access, and integrity) (AWS Documentation: Enabling Amazon S3 server access logging)
- Determining the cause of missing logs and performing remediation steps (AWS Documentation: Remediating security issues discovered by GuardDuty)
Task Statement 2.5: Design a log analysis solution.
Knowledge of:
- Services and tools to analyze captured logs (for example, Athena, CloudWatch Logs filter) (AWS Documentation: Logging and monitoring in Athena)
- Log analysis features of AWS services (for example, CloudWatch Logs Insights, CloudTrail Insights, Security Hub insights) (AWS Documentation: Analyzing log data with CloudWatch Logs Insights)
- Log format and components (for example, CloudTrail logs) (AWS Documentation: CloudTrail log file examples)
Skills in:
- Identifying patterns in logs to indicate anomalies and known threats (AWS Documentation: Log anomaly detection)
- Normalizing, parsing, and correlating logs (AWS Documentation: Parsing logs and structured logging)
Domain 3: Infrastructure Security (20%)
Task Statement 3.1: Design and implement security controls for edge services.
Knowledge of:
- Security features on edge services (for example, AWS WAF, load balancers, Amazon Route 53, Amazon CloudFront, AWS Shield) (AWS Documentation: How AWS WAF works with Amazon CloudFront features)
- Common attacks, threats, and exploits (for example, Open Web Application Security Project [OWASP] Top 10, DDoS)
- Layered web application architecture (AWS Documentation: Three-tier architecture overview)
Skills in:
- Defining edge security strategies for common use cases (for example, public website, serverless app, mobile app backend) (AWS Documentation: Identity and access management)
- Selecting appropriate edge services based on anticipated threats and attacks (for example, OWASP Top 10, DDoS)
- Selecting appropriate protections based on anticipated vulnerabilities and risks (for example, vulnerable software, applications, libraries) (AWS Documentation: Vulnerability Reporting)
- Defining layers of defense by combining edge security services (for example, CloudFront with AWS WAF and load balancers)
- Applying restrictions at the edge based on various criteria (for example, geography, geolocation, rate limit) (AWS Documentation: Restricting the geographic distribution of your content)
- Activating logs, metrics, and monitoring around edge services to indicate attacks (AWS Documentation: Metrics and alarms)
Task Statement 3.2: Design and implement network security controls.
Knowledge of:
- VPC security mechanisms (for example, security groups, network ACLs, AWS Network Firewall) (AWS Documentation: Security best practices for your VPC)
- Inter-VPC connectivity (for example, AWS Transit Gateway, VPC endpoints) (AWS Documentation: Amazon VPC-to-Amazon VPC connectivity options)
- Security telemetry sources (for example, Traffic Mirroring, VPC Flow Logs) (AWS Documentation: Logging IP traffic using VPC Flow Logs)
- VPN technology, terminology, and usage (AWS Documentation: What is AWS Site-to-Site VPN?)
- On-premises connectivity options (for example, AWS VPN, AWS Direct Connect) (AWS Documentation: AWS Direct Connect)
Skills in:
- Implementing network segmentation based on security requirements (for example, public subnets, private subnets, sensitive VPCs, on-premises connectivity)
- Designing network controls to permit or prevent network traffic as required (for example, by using security groups, network ACLs, and Network Firewall) (AWS Documentation: Control traffic to subnets using network ACLs)
- Designing network flows to keep data off the public internet (for example, by using Transit Gateway, VPC endpoints, and Lambda in VPCs) (AWS Documentation: What is a transit gateway?)
- Determining which telemetry sources to monitor based on network design, threats, and attacks (for example, load balancer logs, VPC Flow Logs, Traffic Mirroring) (AWS Documentation: Monitor your Network Load Balancers)
- Determining redundancy and security workload requirements for communication between on-premises environments and the AWS Cloud (for example, by using AWS VPN, AWS VPN over Direct Connect, and MACsec) (AWS Documentation: AWS Direct Connect)
- Identifying and removing unnecessary network access (AWS Documentation: Security best practices in IAM)
- Managing network configurations as requirements change (for example, by using AWS Firewall Manager) (AWS Documentation: Working with AWS Firewall Manager policies)
Task Statement 3.3: Design and implement security controls for compute workloads.
Knowledge of:
- Provisioning and maintenance of EC2 instances (for example, patching, inspecting, creation of snapshots and AMIs, use of EC2 Image Builder) (AWS Documentation: What is EC2 Image Builder?)
- IAM instance roles and IAM service roles (AWS Documentation: IAM roles)
- Services that scan for vulnerabilities in compute workloads (for example, Amazon Inspector, Amazon Elastic Container Registry [Amazon ECR]) (AWS Documentation: Scanning Amazon ECR container images with Amazon Inspector)
- Host-based security (for example, firewalls, hardening)
Skills in:
- Creating hardened EC2 AMIs (AWS Documentation: Create a custom Windows AMI)
- Applying instance roles and service roles as appropriate to authorize compute workloads (AWS Documentation: IAM roles for Amazon EC2)
- Scanning EC2 instances and container images for known vulnerabilities (AWS Documentation: Scanning Amazon EC2 instances with Amazon Inspector)
- Applying patches across a fleet of EC2 instances or container images (AWS Documentation: AWS Systems Manager Patch Manager)
- Activating host-based security mechanisms (for example, host-based firewalls)
- Analyzing Amazon Inspector findings and determining appropriate mitigation techniques (AWS Documentation: Understanding findings in Amazon Inspector)
- Passing secrets and credentials securely to compute workloads (AWS Documentation: AWS security credentials)
Task Statement 3.4: Troubleshoot network security.
Knowledge of:
- How to analyze reachability (for example, by using VPC Reachability Analyzer and Amazon Inspector) (AWS Documentation: Getting started with Reachability Analyzer)
- Fundamental TCP/IP networking concepts (for example, UDP compared with TCP, ports, Open Systems Interconnection [OSI] model, network operating system utilities)
- How to read relevant log sources (for example, Route 53 logs, AWS WAF logs, VPC Flow Logs) (AWS Documentation: Logging IP traffic using VPC Flow Logs)
Skills in:
- Identifying, interpreting, and prioritizing problems in network connectivity (for example, by using Amazon Inspector Network Reachability) (AWS Documentation: Network Reachability)
- Determining solutions to produce desired network behavior (AWS Documentation: AWS Config Managed Rules)
- Analyzing log sources to identify problems (AWS Documentation: Analyzing log data with CloudWatch Logs Insights)
- Capturing traffic samples for problem analysis (for example, by using Traffic Mirroring) (AWS Documentation: What is Traffic Mirroring?)
Domain 4: Identity and Access Management (16%)
Task Statement 4.1: Design, implement, and troubleshoot authentication for AWS resources.
Knowledge of:
- Methods and services for creating and managing identities (for example, federation, identity providers, AWS IAM Identity Center [AWS Single Sign-On], Amazon Cognito) (AWS Documentation: Identity providers and federation)
- Long-term and temporary credentialing mechanisms (AWS Documentation: Use temporary credentials)
- How to troubleshoot authentication issues (for example, by using CloudTrail, IAM Access Advisor, and IAM policy simulator) (AWS Documentation: Troubleshooting AWS CloudTrail identity and access)
Skills in:
- Establishing identity through an authentication system, based on requirements (AWS Documentation: How IAM works)
- Setting up multi-factor authentication (MFA) (AWS Documentation: General steps for enabling MFA devices)
- Determining when to use AWS Security Token Service (AWS STS) to issue temporary credentials (AWS Documentation: Requesting temporary security credentials)
Task Statement 4.2: Design, implement, and troubleshoot authorization for AWS resources.
Knowledge of:
- Different IAM policies (for example, managed policies, inline policies, identity-based policies, resource-based policies, session control policies) (AWS Documentation: Policies and permissions in IAM)
- Components and impact of a policy (for example, Principal, Action, Resource, Condition) (AWS Documentation: IAM JSON policy elements reference)
- How to troubleshoot authorization issues (for example, by using CloudTrail, IAM Access Advisor, and IAM policy simulator) (AWS Documentation: Troubleshooting AWS CloudTrail identity and access)
Skills in:
- Constructing attribute-based access control (ABAC) and role-based access control (RBAC) strategies (AWS Documentation: What is ABAC for AWS?)
- Evaluating IAM policy types for given requirements and workloads (AWS Documentation: Policy evaluation logic)
- Interpreting an IAM policy’s effect on environments and workloads (AWS Documentation: IAM policy elements: Variables and tags)
- Applying the principle of least privilege across an environment
- Enforcing proper separation of duties
- Analyzing access or authorization errors to determine cause or effect (AWS Documentation: Using AWS Identity and Access Management Access Analyzer)
- Investigating unintended permissions, authorization, or privileges granted to a resource, service, or entity (AWS Documentation: Managing access permissions for your AWS organization)
Domain 5: Data Protection (18%)
Task Statement 5.1: Design and implement controls that provide confidentiality and integrity for data in transit.
Knowledge of:
- TLS concepts (AWS Documentation: Transport Layer Security (TLS))
- VPN concepts (for example, IPsec) (AWS Documentation: What is a VPN (Virtual Private Network)?)
- Secure remote access methods (for example, SSH, RDP over Systems Manager Session Manager) (AWS Documentation: AWS Systems Manager Session Manager)
- Systems Manager Session Manager concepts
- How TLS certificates work with various network services and resources (for example, CloudFront, load balancers) (AWS Documentation: TLS listeners for your Network Load Balancer)
Skills in:
- Designing secure connectivity between AWS and on-premises networks (for example, by using Direct Connect and VPN gateways) (AWS Documentation: AWS Direct Connect )
- Designing mechanisms to require encryption when connecting to resources (for example, Amazon RDS, Amazon Redshift, CloudFront, Amazon S3, Amazon DynamoDB, load balancers, Amazon Elastic File System [Amazon EFS], Amazon API Gateway) (AWS Documentation: Encrypting Amazon RDS resources)
- Requiring TLS for AWS API calls (for example, with Amazon S3) (AWS Documentation: Infrastructure security in Amazon S3)
- Designing mechanisms to forward traffic over secure connections (for example, by using Systems Manager and EC2 Instance Connect) (AWS Documentation: Connect using EC2 Instance Connect)
- Designing cross-Region networking by using private VIFs and public VIFs
Task Statement 5.2: Design and implement controls that provide confidentiality and integrity for data at rest.
Knowledge of:
- Encryption technique selection (for example, client-side, server-side, symmetric, asymmetric) (AWS Documentation: AWS KMS concepts)
- Integrity-checking techniques (for example, hashing algorithms, digital signatures) (AWS Documentation: Checking object integrity)
- Resource policies (for example, for DynamoDB, Amazon S3, and AWS Key Management Service [AWS KMS]) (AWS Documentation: Key policies in AWS KMS)
- IAM roles and policies (AWS Documentation: Policies and permissions in IAM)
Skills in:
- Designing resource policies to restrict access to authorized users (for example, S3 bucket policies, DynamoDB policies) (AWS Documentation: Examples of Amazon S3 bucket policies)
- Designing mechanisms to prevent unauthorized public access (for example, S3 Block Public Access, prevention of public snapshots and public AMIs) (AWS Documentation: Blocking public access to your Amazon S3 storage)
- Configuring services to activate encryption of data at rest (for example, Amazon S3, Amazon RDS, DynamoDB, Amazon Simple Queue Service [Amazon SQS], Amazon EBS, Amazon EFS) (AWS Documentation: Encryption at rest in Amazon SQS)
- Designing mechanisms to protect data integrity by preventing modifications (for example, by using S3 Object Lock, KMS key policies, S3 Glacier Vault Lock, and AWS Backup Vault Lock) (AWS Documentation: Using S3 Object Lock)
- Designing encryption at rest by using AWS CloudHSM for relationaldatabases (for example, Amazon RDS, RDS Custom, databases on EC2 instances)
- Choosing encryption techniques based on business requirements (AWS Documentation: Creating an enterprise encryption strategy for data at rest)
Task Statement 5.3: Design and implement controls to manage the lifecycle of data at rest.
Knowledge of:
- Lifecycle policies
- Data retention standards
Skills in:
- Designing S3 Lifecycle mechanisms to retain data for required retention periods (for example, S3 Object Lock, S3 Glacier Vault Lock, S3 Lifecycle policy) (AWS Documentation: Managing your storage lifecycle)
- Designing automatic lifecycle management for AWS services and resources (for example, Amazon S3, EBS volume snapshots, RDS volume snapshots, AMIs, container images, CloudWatch log groups, Amazon Data Lifecycle Manager) (AWS Documentation: Amazon Data Lifecycle Manager)
- Establishing schedules and retention for AWS Backup across AWS services (AWS Documentation: Creating a backup plan)
Task Statement 5.4: Design and implement controls to protect credentials, secrets, and cryptographic key materials.
Knowledge of:
- Secrets Manager (AWS Documentation: What is AWS Secrets Manager?)
- Systems Manager Parameter Store (AWS Documentation: AWS Systems Manager Parameter Store)
- Usage and management of symmetric keys and asymmetric keys (for example, AWS KMS)
Skills in:
- Designing management and rotation of secrets for workloads (for example, database access credentials, API keys, IAM access keys, AWS KMS customer managed keys)
- Designing KMS key policies to limit key usage to authorized users (AWS Documentation: Key policies in AWS KMS)
- Establishing mechanisms to import and remove customer-provided key material (AWS Documentation: Importing key material for AWS KMS keys)
Domain 6: Management and Security Governance (14%)
Task Statement 6.1: Develop a strategy to centrally deploy and manage AWS accounts.
Knowledge of:
- Multi-account strategies (AWS Documentation: Organizing Your AWS Environment Using Multiple Accounts)
- Managed services that allow delegated administration (AWS Documentation: AWS services that you can use with AWS Organizations)
- Policy-defined guardrails
- Root account best practices (AWS Documentation: Root user best practices for your AWS account)
- Cross-account roles (AWS Documentation: Delegate access across AWS accounts using IAM roles)
Skills in:
- Deploying and configuring AWS Organizations (AWS Documentation: Creating and configuring an organization)
- Determining when and how to deploy AWS Control Tower (for example, which services must be deactivated for successful deployment) (AWS Documentation: Deploying AWS Control Tower in an AWS Landing Zone organization)
- Implementing SCPs as a technical solution to enforce a policy (for example, limitations on the use of a root account, implementation of controls in AWS Control Tower)
- Centrally managing security services and aggregating findings (for example, by using delegated administration and AWS Config aggregators) (AWS Documentation: How central configuration works)
- Securing AWS account root user credentials (AWS Documentation: AWS security credentials)
Task Statement 6.2: Implement a secure and consistent deployment strategy for cloud resources.
Knowledge of:
- Deployment best practices with infrastructure as code (IaC) (for example, AWS CloudFormation template hardening and drift detection) (AWS Documentation: AWS CloudFormation best practices)
- Best practices for tagging (AWS Documentation: Best Practices for Tagging AWS Resources)
- Centralized management, deployment, and versioning of AWS services
- Visibility and control over AWS infrastructure
Skills in:
- Using CloudFormation to deploy cloud resources consistently and securely (AWS Documentation: AWS CloudFormation best practices)
- Implementing and enforcing multi-account tagging strategies (AWS Documentation: Implementing and enforcing tagging)
- Configuring and deploying portfolios of approved AWS services (for example, by using AWS Service Catalog) (AWS Documentation: Automate AWS Service Catalog portfolio and product deployment by using AWS CDK)
- Organizing AWS resources into different groups for management (AWS Documentation: What are resource groups?)
- Deploying Firewall Manager to enforce policies (AWS Documentation: Working with AWS Firewall Manager policies)
- Securely sharing resources across AWS accounts (for example, by using AWS Resource Access Manager [AWS RAM]) (AWS Documentation: Shareable AWS resources)
Task Statement 6.3: Evaluate the compliance of AWS resources.
Knowledge of:
- Data classification by using AWS services (AWS Documentation: Data classification overview)
- How to assess, audit, and evaluate the configurations of AWS resources (for example, by using AWS Config) (AWS Documentation: Evaluating Resources with AWS Config Rules)
Skills in:
- Identifying sensitive data by using Macie (AWS Documentation: Discovering sensitive data with Amazon Macie)
- Creating AWS Config rules for detection of noncompliant AWS resources (AWS Documentation: Remediating Noncompliant Resources with AWS Config Rules)
- Collecting and organizing evidence by using Security Hub and AWS Audit Manager (AWS Documentation: Reviewing the evidence in an assessment)
Task Statement 6.4: Identify security gaps through architectural reviews and cost analysis.
Knowledge of:
- AWS cost and usage for anomaly identification (AWS Documentation: Getting started with AWS Cost Anomaly Detection)
- Strategies to reduce attack surfaces (AWS Documentation: Attack surface reduction)
- AWS Well-Architected Framework (AWS Documentation: AWS Well-Architected Framework)
Skills in:
- Identifying anomalies based on resource utilization and trends (AWS Documentation: Using CloudWatch anomaly detection)
- Identifying unused resources by using AWS services and tools (for example, AWS Trusted Advisor, AWS Cost Explorer) (AWS Documentation: Analyzing your costs with AWS Cost Explorer)
- Using the AWS Well-Architected Tool to identify security gaps (AWS Documentation: Security in AWS Well-Architected Tool)
AWS Specialty Security Exam Preparation Resources
For AWS Security Specialty exam there are many resources that are available both online and offline which will help you during preparation for the exam. This will help you in understanding the topics better and also provide an expert assistance to solve your queries. Here we provide you the learning resources to get the most from your efforts in the AWS Certified Security Specialty study guide.
AWS Security Specialty Recommended Books
The AWS certified security specialty book are a perennial source available for learning. There are various books available for the security specialty exam which you can find online or in libraries. Some of the books that can arm you are as follows:
- AWS: Security Best Practices on AWS – By Albert Anthony
- Mastering AWS Security: Create and Maintain a Secure Cloud Ecosystem By Albert Anthony
- Cloud Security Automation – Get to grips with automating your Cloud Security on AWS and OpenStack by Prashant Priyam
And there are many websites available which provide online training for the exam with a full assistance to the course such as Simplilearn, Pluralsight, udemy and many more.
Discussion Forums
Many websites provide good information and topic details related to the certification which can be helpful when having any doubt or want to know something about the exam. Some of them are,
- Answers.com
- Quora
- Stackoverflow
Practice Questions
Practice questions for the AWS Certified Security Specialist might help you study more effectively and move more quickly. As a result, when you finish, there are many websites that provide practice exams and assess you based on your expertise and understanding of AWS Security Services. On Amazon, you may also look for practice sets, although not all of the topics will be included. At Testprep Training you get a bulk of practice sets of questions on the AWS Security Specialty exam in two ways,
- Free practice questions for AWS Security Specialty exam
- Real time practice questions for AWS Security Specialty exam with detailed analysis.
Training at AWS
There are many free training that is provided for AWS Security Specialty exam at https://aws.amazon.com/training/. These AWS certified security specialty training require registration and are available at zero cost. AWS also gives access to various Learning libraries to get you know more about the AWS services. AWS also includes AWS APN partner which helps you to accelerate your business on AWS
What are the benefits of AWS Certified Security Specialty?
The AWS Certified Security – Specialty certification provides a number of benefits to IT professionals and organizations that use AWS. Some of the key benefits include:
- Career advancement: The AWS Certified Security – Specialty certification is recognized as a benchmark of expertise in securing AWS workloads, and can help IT professionals advance their careers and increase their earning potential.
- Increased credibility: The AWS Certified Security – Specialty certification provides IT professionals with an industry-recognized credential that demonstrates their expertise in securing AWS workloads. This credibility can help IT professionals stand out in a competitive job market.
- Improved job performance: The AWS Certified Security – Specialty certification provides IT professionals with a deep understanding of security best practices and AWS security services. This knowledge can help IT professionals improve their job performance and deliver more secure AWS workloads.
- Staying current with AWS updates: Earning the AWS Certified Security – Specialty certification requires staying current with updates to the AWS platform, which can help IT professionals stay current with the latest security features and capabilities of AWS.
- Better security for AWS workloads: The knowledge and skills gained through the AWS Certified Security – Specialty certification can help IT professionals design and implement more secure AWS workloads, reducing the risk of security breaches and data loss.
- Increased confidence and competitiveness: The AWS Certified Security – Specialty certification provides IT professionals with the confidence and credibility they need to compete for new job opportunities and succeed in their careers.
AWS Security Learning Path
This learning path is intended for those who carry out security-related tasks and want to feel in charge and confident when running apps on the Amazon cloud. You will learn about data encryption techniques, application security, and access control in this. You should get some expertise using the Amazon cloud for a specialty domain before applying.
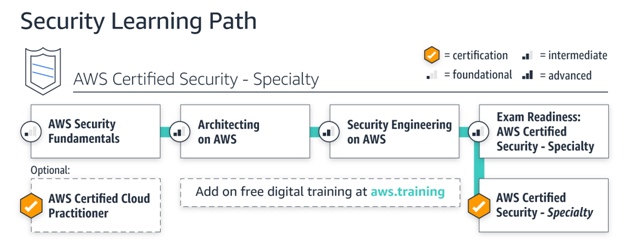
“AWS Security Specialty exam will provide an advantage in enhancing your skills and experience in security solutions for securing AWS platform. For preparation of exam, tips are provided below and for tutorial you can reach out AWS Security Specialty tutorials.”
Preparing for AWS Security Specialty exam
For the preparation of this certification exam it is important that you should make a good mindset that you have to and you should pass this certification anyhow. This will require a disciplined schedule for studying for the examination as well as it is also important that you should have experience and practical knowledge in security solutions. This certification will open doors for many new opportunities and will improve your skills and knowledge.
Exam Tips:
- Familiarize yourself with the exam format: Understanding the format of the exam and the types of questions that will be asked can help you better prepare and increase your chances of success.
- Review the AWS Security Fundamentals: Familiarize yourself with the core security concepts and technologies used in AWS.
- Study the AWS Well-Architected Framework: The Well-Architected Framework provides best practices for designing secure and scalable AWS workloads.
- Use AWS official training resources: AWS provides a range of official training resources, including whitepapers, online courses, and certification preparation workshops, to help you prepare for the exam.
- Practice using AWS services: Hands-on experience is key to success on the exam. Practice using AWS security services such as Amazon Virtual Private Cloud (VPC), AWS Identity and Access Management (IAM), and AWS Key Management Service (KMS) to build a solid understanding of how they work.
- Create a study plan and stick to it: Create a study plan that works for you and stick to it. This can help you focus your efforts and make the most of your study time.
- Practice with mock exams: Practicing with mock exams can help you identify areas where you need to improve and get a feel for the types of questions that will be on the real exam. Free practice questions for AWS Security Specialty exam
- Seek out additional resources: Look for additional resources, such as study guides and practice exams, that can help you prepare for the exam.
Remember, the AWS Certified Security – Specialty certification is a challenging exam, and preparation and hard work are key to success. By following these tips and using the resources available, you can increase your chances of success on the exam and become an AWS Certified Security – Specialty.

